As a blogger, I always enjoy the comments on my writing a lot. I do not always follow up on them as accurately as I would like to, but trust me when I say I do enjoy them.
A couple of days ago I received mail from Vaughan Armstrong. I met Mr. Armstrong once at Aloa and learned he is a well respected authority in the field of US military locks and safes.
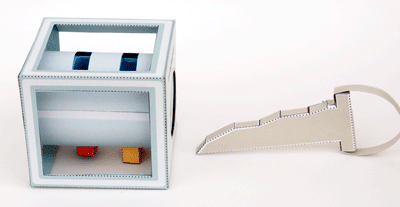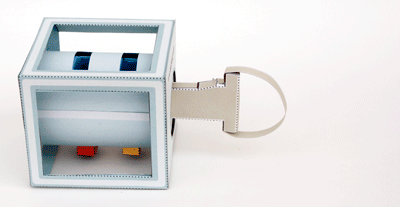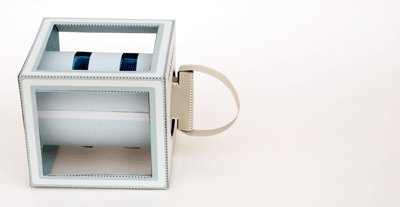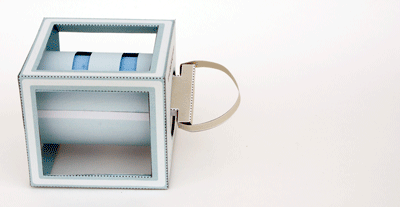
So I was thrilled to read Mr. Armstrong took his time to answer some of my (our) burning questions. As frequent readers of this weblog might remember, I received a nice US DoD safe (GSA security container) some time ago. When I got it, there were a lot of questions (as you can read in the original post). But thanks to Mr. Armstrong we now know a lot more:
I have read the posts regarding Barry’s Christmas present (December 2006). My thanks to all who posted; I would like to contribute some information.
The present is a field safe, a GSA (General Services Administration) approved security container, for storage of classified material in the field. Federal Specification AA-F-358 (current revision H),(18 May 2000) and its most recent Amendment (3),(20 April 2007) give the requirements for this “Class 6, Size VIII 1-drawer, for field use.” To view the Specification, visit the Department of Defense Lock Program’s website, https://portal.navfac.navy.mil/go/locks . Put your cursor on “Documents.” Several choices will appear in the drop-down; click on “Federal Specifications and QPLs,” and scroll down to AA-F-358H.
This is a Class 6 container; as with all Class 6 containers currently produced, it provides 30 man-minutes of covert entry protection, 20 man-hours of surreptitious entry protection, and is not tested for forced entry protection. (For definitions of “covert” and “surreptitious,” see paragraphs 6.4.3 and 6.4.2.) Because it is for use in the field, paragraph 3.3.8 requires that “The Class 6, Size VIII cabinet shall be provided with 2 lift type carrying handles” and paragraph 3.3.8.2 requires that it have a dial knob protector (visible in the photograph).
The red-lettered label on the front of the drawer indicates that it was made between October 1, 1990 and present. The drawerhead is removable from the rest of the drawer.
Paragraph 3.3, Table I gives maximum dimensions and weights for containers covered by the Specification; the weight of the Christmas present is within the limit (maximum weight 138 lbs.) for field safes. Paragraph 3.3.2 requires that “The weight shall be permanently marked” on the container.
Paragraph 3.4.2 addresses the lock required. It now must be approved to the requirements of Federal Specification FF-L-2937. Previously, locks meeting Underwriters Laboratories (UL) 768, Group 1R were required. The lock must have a snap-on dust cover. This is to prevent someone “dusting” the dial and dial ring to determine the combination. (Some people use a thumb as a “brake” to steady the dial when approaching a target number. This leaves half a thumbprint on the dial ring and half a thumbprint in three locations on the dial. There are only six ways that these indications can be combined: A-B-C, A-C-B, B-A-C, B-C-A, C-A-B, and C-B-A, and these can be entered in a very short time.) The original lock on this container was the S&G 8560MP.
To visit Hamilton Products Group’s website, from the home page of the DoD Lock Program website, put cursor on “Links Index,” scroll down to “Hamilton Products Group” and click on it. You’ll see that the field safe is made in a single-lock and a dual-lock version.
I hope this has been informative, and possibly interesting.
Vaughan Armstrong
I would like to thank Mr. Armstrong for taking his time to answer the open questions (especially on the dustcover) on this little humble weblog. Hopefully it will not be his last comment here.