Laura Balver of the Dutch program ‘Ik op TV’ visited Toool Amsterdam. Click to see Dutch clip….
‘Ik op TV’
February 20th, 2008Back from Spain …
February 17th, 2008Phew … I made it … here is the Sunday Blackbag posting of the week …
I made the most of my days in Barcelona. From 09:00 to 19:00 I was behind the booth at the 3GSM show, never to return home before 01:00 from meetings with Spanish lockpickers and locksmiths.
Very generous people I met, as I ended up with 55 kilo’s(!) of locks and blanks. Enough to keep me busy for quite some time….
Normally I would not have been able to transport all this precious metal. Luckily for me, a Dutch friend (Vincent ‘Norman’ Vlaming) was doing his internship at our company, and he and his father helped me out by taking kilos and kilos of locks in their luggage.
But back to Spanish locks: A high number of lever locks are in use there, as well as lots of dimple locks.

Some of the lever locks (Orenco for example) have something remarkable. The keys miss a small part at the bottom, making the lower finger of the key stick out a little. This is the part that keeps the lock under pressure. This is a cheap and simple counter measure to avoid opening the lock using a classic hobbs pick. There just is no room for the tensioner of the Hobb’s pick, as a little ring deep inside the lock takes away all the space.
As it is a popular lock, of course there is a pick for it. And I got a demonstration of it. Unfortunately I did not shoot any photo’s, but it is a classical Hobb’s pick and … a hollow file (tube shaped). The file is inserted into the lock and the ring at the bottom of the lock is simply filed away. After removing that part, the classic Hobb’s pick can be used to open the lock.

I have also seen some special and remarkable models. Take for instance this Inceca lock with it’s round key. I have not tried, but people told me it can be opened relatively quickly with a sort of tubular pick.
Another special lock was the JIS, with it’s two rows and nine pins.
Twenty of the most interesting Spanish locks will be used in the 2008 Toool competition. The JIS lock will be in it for sure, so we will soon know if two rows of pins make life real difficult for us lockpickers. We always shoot high quality images of the competition locks, so … stay tuned for more Spanish lock info…
Barcelona
February 11th, 2008I am right now in Barcelona. Unfortunately the internet connection at the apartment we rented is broken, so this message is written from an internet cafe (and in a hurry) …
The good news is I met a local locksmith yesterday that gave me a ‘small present’ … A box containing 25 Kilograms of locks!
There are some real treasures in this big box, and when I am back in Amsterdam I will make some nice detailed images of some of them.
It contains lots of dimple locks, some ‘normal’ pin tumbler locks and also many lever locks! Real nice, real weird sometimes …
The blanks I brought with me cover 50% of the (pin tumbler) locks I received. Not a bad score. Tonight I will try to impression a few locks, and teach the friendly locksmiths the basics of impressioning….
Barry in Barcelona …
February 6th, 2008End of the week I will be visiting Barcelona for a couple of days. To be more precise, from Sunday 10 to Thursday 14 February I will be at the CryptoPhone stand at the 3GSM show.
Whenever I travel abroad I try to estimate the most common locks and order (ten of each of) the most popular blanks. In case of Spain I understood they use a lot of dimple locks like TESA T-60 and T-80, MCM 4SE, CISA, STS (CS-5, CS-6, CS-8 etc), ISEO, Ezcurra S-10 and DS-15 and LINCE. So I collected around twenty different type of blanks. Of course this is not enough to cover all the locks, but I hope it covers some of them.
As far as I see, Impressioning dimple locks is the same as impressioning a ‘normal’ pin tumbler locks. Problem is I only tried around ten different locks (Iseo, Lips, Dom, Keso, Abus, Mul-t 7X7 etc). And except the mul-t-lock 7X7 I succeeded in opening all of them. I hope to get my hands on some (used) spanish dimple locks while there and be able to practice some more.
Are there Spanish blackbag readers that would like to meet for a cup of coffee, and maybe trade locks and/or blanks? I will be staying in the Plaza España area in Barcelona.
Advice on what other locks/blanks are popular in Spain is welcome too, please use the comments (or mail me: barry at toool.nl) if you have any info….
how it’s made: cutting the profile in the lock core
February 4th, 2008I must admit I have been so busy last week that making the sunday evening deadline was not easy.
But hey, a promise is a promise … so here goes another posting …
I was planning on writing something about Marc Tobias his hack on alarm systems. The weak spot are the wireless sensors (operating on 433.92 Mhz). Maybe I will get back to that later.
Today I want to talk about some of the fun things at Toool: factory visits!
Dutch lock company Anker invited us last year for a factory visit. Even while most of the well respected brands on the market have lots of their parts made in China, Dutch lock company Anker is an exception. They still do most of the work in their own factory, and are very proud of that. At least in the Netherlands they are unique in that respect.
The following video will show you how the key profile is cut into a lock core. Anker is known by us lockpickers by their nasty to pick profiles: very narrow, lot of zig-zag’s and six pins. Not completely impossible, but by no means easy.
In this video you will learn how the profile is cut in the lock core (quicktime or youtube).
Sunday movie premiere: The russian lock … Part II
January 28th, 2008Do you remember the mysterious Russian lock?
The one used by Russian Government to safeguard their (nuclear) secrets?
Over a year ago I did a posting on this special and very rare lock. I strongly encourage you to read this previous posting if you don’t know what I am talking about. (Click on this link)
In the previous video (windows media 77 MB) the lock is only slightly disassembled.

Today, safe technician Oliver Diederichsen will show you more. He will try to go all the way and fully disassemble the Russian lock to make it reveal it’s secrets.
Personally I was very curious what locking mechanisms were inside.
Keep in mind, this is/was the top of the line in ‘cold war’ Russian lock technology, meant to keep out some of the most clever adversaries (with unlimited budgets). Someone who is not into locks probably thinks this is a boring video. For me, it comes close to viewing an autopsy on a space alien.
See the autopsy of the Russian lock in: The Russian lock part II … (9 minutes, Quicktime movie 55 MB)
More high quality images of this lock (and many other interesting things) can be found on the webpage of Eric Schmiedl (Toool.US).
Unstealable police car …. stolen!
January 21st, 2008unpickable locks get picked, unstealable cars get stolen ….
‘Theft-proof’ police car stolen
A high tech, theft-proof £75,000 police car was stolen in Berlin – after officers left it unlocked with the key in the ignition.
The special BMW, which features high-tech surveillance equipment and sophisticated electronic locks and immobilisers to make it theft proof, was the pride of the Berlin police force.
But it was stolen in the city’s Wedding district when two officers jumped out to chase a joy-rider on foot after he had abandoned a stolen car.
The criminal got away and when the officers went back they found the expensive BMW gone.
The pair are facing disciplinary action. Police chiefs say they have no leads on who may have stolen the car and are still looking for it.
* note Barry: The car was an unmarked police car, used for traffic enforcement. The ‘high-tech surveillance equipment ‘ is probably nothing more then the latest generation video and speed measurement gear. My suggestion for the traffic police: keep an eye out on ebay.de ….)
UK locksmiths and rubber gloves …
January 21st, 2008Maybe from now on UK locksmiths will be wearing rubber gloves ….
BURGLAR? NOT ME, I’M JUST THE LOCKSMITH
18 January 2008
Locksmith Lee Hicks was arrested for burglary when police found his fingerprints on locks he’d fixed – after the raid.Officers swooped on his Tewkesbury home and held him in custody for three hours.
They’d found his fingerprints at a garage that had been burgled, and assumed he was their man.
But he had been called to replace the locks the real burglars had broken.
His frightened wife and two young children looked on in disbelief as officers rummaged through wardrobes searching for evidence at 6am on Wednesday.
He tried to explain to the police why his fingerprints were at the scene of the crime.

But Lee was bundled into the back of a van and whisked off to Cheltenham Police Station.
The 33-year-old says he was shown no sympathy and treated like a criminal during his four hours in custody.
Now he is considering suing Gloucestershire Police for wrongful arrest. He said the whole thing was “unbelievable” .
He was called to change the locks at a petrol station in Newent on June 4 last year.
Raiders had smashed their way in and stolen a large number of cigarettes.
Because Lee had been in trouble with the law when he was younger, the police had his fingerprints on file.
Officers found his prints at the garage but Lee said they did not ask staff if a locksmith had been there.
Instead, they mounted a dawn raid, seven months later.
He said: “There was a loud bang on the door. There were three male police officers and one female officer. I was put into the back of a van with a cage in it.”
When he told officers at the police station they had made a mistake, the desk sergeant told him everyone claimed to be innocent.
Lee, who lives in Sallis Close, Northway, spent three hours in a cell waiting to be questioned.
He said: “They took my top from me because it had cords attached. I was shivering.
“When they finally questioned me, it was for less than five minutes.”
He is angry and amazed that the police took seven months to arrest the wrong man.
He said: “They took four hours of my life and the impression I got was they just didn’t care.
“I want someone from the police’s hierarchy to read this and think ‘this needs looking into and we can’t treat people like this’.
“It was hard to accept being locked up when you hadn’t done anything wrong.”
But Gloucestershire Police say they were right to arrest him.
Spokeswoman Kate Nelmes said he was released without charge after officers got proof he was a locksmith.
She said: “His fingerprints were picked up at the garage. It’s obvious he would be arrested. We wouldn’t know he was a locksmith or what he was doing there.”
ultraviolet impressioning
January 20th, 2008Sunday is blackbag day, so here is my sunday posting:
Impressioing is still part of my daily routine. I used to open at least one lock per day, now I sometimes skip a few days and open five locks in a row… Occasionally I have to open a lock a different way and take it apart to see why impressioning did not work, but it does not happen often.
I keep experimenting with new techniques and try to open more sophisticated locks. And I invest a lot of time learning about blanks, and keep searching for exotic keyblanks. (if you have any interesting european or US blanks, please drop me a mail)
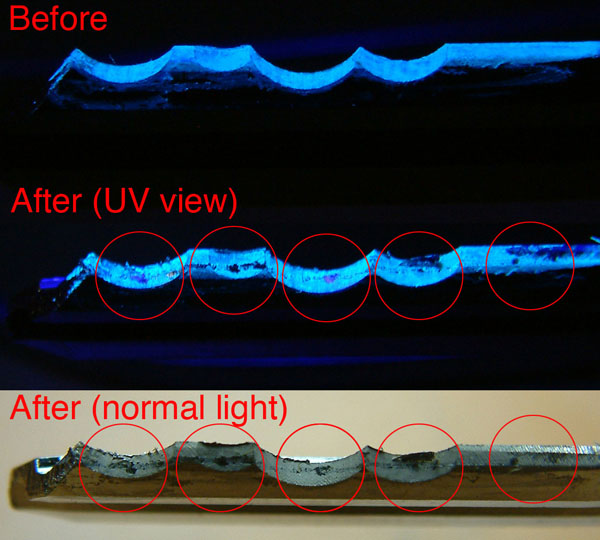
This weekend I experimented a little on using ultraviolet light and UV ink.
I was hoping ultraviolet light would point out some marks that are difficult to see under normal light conditions. So far this is has not been very successful as I could see approximately 80% of the marks I normally see. And it slows me down as it takes the ink between 45 and 60 seconds to dry. Then again, I just started using this technique … and it is nothing more then an experiment and gaining knowledge and experience.
I shot some images for my dear readers, so you might want to click on them:
1) First round of impressioning (UV and TL view)
2) Second round of impressioning (UV and TL view)
3) Sixth round of impressioning (before and after)
4) Marker, includes advice (Edding 8280)
5) Forensic evidence, ink residue on the lock
For this experiment I used a Q22 inspection light (UVA light, 360 nm, the least harmful of the ultraviolet spectrum) and an edding 8280 marker.
Next week on blackbag: video revealing more of the inner workings of the mysterious ‘russian lock‘ ….
Dutch OV Chipkaart haunted by ghosts
January 15th, 2008This is getting embarrassing… Yesterday Roel Verdult of Nijmegen’s radboud university demonstrated on Dutch television (WMV or Youtube) how he hacked the disposable RFID public transport card. Roel created a small device called ‘ghost’ that is capable of cloning disposable cards and re-use them over and over again. Total hardware costs around 40 euro. And Roel thinks as soon as the German researchers release their information on Mifare classic, the ‘more secure’ subscription tickets can also be cloned . Some english information from his hand is available here (pdf).
This is the second time this card is hacked in a short time, yet the designers of the system (translink systems) say there is nothing to worry about, and the system still is ‘very secure’. *sigh*.
Talking about depressive: some information just came out about privacy issues with the OV Chipkaart (WMV). All travel data is stored for seven(!) years. And the stored data is ‘not very well protected’ ….