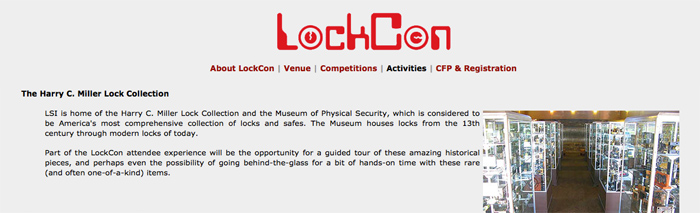
The LockCon 2011 announcement It’s about time
The big question always is: how to pack a four of five day event in just one weekend? The answer lies in the (preliminary) LockCon 2011 schedule:
Friday, October 21 2011
Visitors are advised to arrive before 18:00 (if possible). Toool representatives will be present in the hostel from Thursday on, and be available all day to assist visitors and assign them rooms and explain the (simple) rules of the event.
18:00 – 19:00. Dinner will be served. We hope the kitchen stays open till 19:30/19:45 for latecomers.
Friday 20:30 – 21:30 “Masterkeys for a non-masterkeyed system” by Han Fey
 Han Fey likes to investigate. On the second hand market he found locks from a facility with180 individual locks. These locks were not masterkeyed. Han did however discover a flaw in the system, allowing a relatively small set of try-out keys to open all the locks. In this presentation he goes into detail how he identified the flaw, narrowed down the keyspace and optimized his attack. Fascinating material.
Han Fey likes to investigate. On the second hand market he found locks from a facility with180 individual locks. These locks were not masterkeyed. Han did however discover a flaw in the system, allowing a relatively small set of try-out keys to open all the locks. In this presentation he goes into detail how he identified the flaw, narrowed down the keyspace and optimized his attack. Fascinating material.
Saturday, October 22 2011
08:00 – 09:00 Breakfast.
Saturday 09:00 – 14:00 “5 hours, 50 locks, 500 slides” By Peter Field
(Includes Lunch around 12:00)
As many LockCon attendees know, Peter Field has an extraordinary way of looking at locks. Like a pathologist, he cuts locks in many thin slices and captures the result with high quality photography. This unique methods of creating a cutaway view is world renowned. With it he has set a standard many people tried to copy but only very few can even get close.

We are proud and honored to have Peter over for yet another long presentation about the different elements in high security cylinder lock design. Combining his unique cut-away imagery with illustrations from old patents, he will explain how engineers classify the cylinder elements, modify them, develop new ones, and re-combine them all to invent new products for the constantly evolving security market. You will leave this presentation with an outline and a clear understanding of the design constraints and functions of most of the various elements you may find in any lock cylinder.
About Peter Field: he started locksmithing in 1960, and in 1978 was asked to join Medeco Security Locks, where he is now Director of Research. He has over 15 US Patents pertaining to high security locks, with several more patents pending. Being a employee of Medeco one thing is clear: Mr. Field will not discuss any opening techniques. As he told us in previous years: “I am here to talk about locks. How to open them is up to you ….”.
15:00 – 15:45 “State of the art locks in the Stasi era” by Oliver Diederichsen
 Oliver Diederichsen managed to get his hands on some unique material: complete Stasi manuals of the department responsible for covert entry operations. Many of the techniques and tools can still be converted to work on modern locks. Oliver will highlight one part of the files that talks about the state of the art in locks around the late eighties, and how far the stasi got in bypassing them.
Oliver Diederichsen managed to get his hands on some unique material: complete Stasi manuals of the department responsible for covert entry operations. Many of the techniques and tools can still be converted to work on modern locks. Oliver will highlight one part of the files that talks about the state of the art in locks around the late eighties, and how far the stasi got in bypassing them.
16:00 – 17:00 “Magnetic locks and how to defeat them” by Datagram
 Datagram is a well known expert in the field of lock forensics, but also does lots of other interesting research. Magnetic locks are still considered amongst the most high-secure locks. And in some cases rightfully so. During his presentation Datagram will show what progress he made on bypassing some of these magnetic locks, and demonstrate his custom made opening and decoding tool.
Datagram is a well known expert in the field of lock forensics, but also does lots of other interesting research. Magnetic locks are still considered amongst the most high-secure locks. And in some cases rightfully so. During his presentation Datagram will show what progress he made on bypassing some of these magnetic locks, and demonstrate his custom made opening and decoding tool.
17:15 – 18:00 “Impressioning Abloy Classic” by Jaakko Fagerlund
 Jaakko Fagerlund is a big fan of Abloy locks and knows a lot about them. And of course he is interested how to tackle the system/ Together with Jord Knaap they improved on Barry Wels his ‘reduced contact area‘ impressioning technique for disc-locks. They found a way to get better marks and make the process more easy, and share their findings in this workshop.
Jaakko Fagerlund is a big fan of Abloy locks and knows a lot about them. And of course he is interested how to tackle the system/ Together with Jord Knaap they improved on Barry Wels his ‘reduced contact area‘ impressioning technique for disc-locks. They found a way to get better marks and make the process more easy, and share their findings in this workshop.
18:00-19:00 dinner
20:00 – 23:00 Impressioning championships.

Impressioning is the fine art of opening a lock by filing a key from a blank. It is an ancient technique that still works on an amazing number of (high security) locks. The championships speak for themselves: who will be the fastest filing a working key to a lock his year? The impressioning championships will be played by the new rules. Meaning 45 people start with impressioning the same lock, and the first six people to open the lock will move on to the finals. Abus reserved some old stock just for these games and donated the C83 cylinders and blanks again this year. Thank you Abus!
Sunday October 23
08:00 – 09:30 Breakfast.
10:00 – 11:00 “Fichet F3D lock analysis” by Michael Huebler
 The Fichet F3D lock is one of the most intriguing locks that came out in a long time. Not easy to get, quite expensive and contains many, many parts. The innner working of the lock also is quite interesting and unique. Michael will take you trough the lock step by step, and there will be an interesting discussion on how this lock maybe could be bypassed.
The Fichet F3D lock is one of the most intriguing locks that came out in a long time. Not easy to get, quite expensive and contains many, many parts. The innner working of the lock also is quite interesting and unique. Michael will take you trough the lock step by step, and there will be an interesting discussion on how this lock maybe could be bypassed.
11:30 – 15:30 Dutch Open lockpick championships.
 We are not going to play the one-on-one, and ‘winner takes all” that we did last year. It will be fair and balanced how we do it, and it will allow for many small picking contests against a direct opponent. In these games two people will be playing against each other, and the one with the most locks opened, or the fastest time if the same amount of locks are opened, will go trough to the next round. If the two contestants do not manage to open any of the locks they are both out of the game. In case we have an odd number of contestants, there will be three people competing against each other and the fastest two go trough. The last man standing wins!
We are not going to play the one-on-one, and ‘winner takes all” that we did last year. It will be fair and balanced how we do it, and it will allow for many small picking contests against a direct opponent. In these games two people will be playing against each other, and the one with the most locks opened, or the fastest time if the same amount of locks are opened, will go trough to the next round. If the two contestants do not manage to open any of the locks they are both out of the game. In case we have an odd number of contestants, there will be three people competing against each other and the fastest two go trough. The last man standing wins!
There always is question about the selection of locks that will be used in the game. The brands will be kept secret, but we will try to arrange just two types of locks and make sure one of these locks is ‘relatively simple’ to open by an experienced picker. The locks used will be ‘standard’ five or six pin locks (so no dimple locks or special high security locks in the finals).
16:00 honoring the LockCon champs
17:00 Early dinner for those who need to travel
More information on how to register for LockCon2011 can be found here.
Expect this posting to change a little in the days to come.









 Han Fey likes to investigate. On the second hand market he found locks from a facility with180 individual locks. These locks were not masterkeyed. Han did however discover a flaw in the system, allowing a relatively small set of try-out keys to open all the locks. In this presentation he goes into detail how he identified the flaw, narrowed down the keyspace and optimized his attack. Fascinating material.
Han Fey likes to investigate. On the second hand market he found locks from a facility with180 individual locks. These locks were not masterkeyed. Han did however discover a flaw in the system, allowing a relatively small set of try-out keys to open all the locks. In this presentation he goes into detail how he identified the flaw, narrowed down the keyspace and optimized his attack. Fascinating material. 
 Oliver Diederichsen managed to get his hands on some unique material: complete
Oliver Diederichsen managed to get his hands on some unique material: complete  Datagram is a well known expert in the field of
Datagram is a well known expert in the field of  Jaakko Fagerlund is a big fan of Abloy locks and knows a lot about them. And of course he is interested how to tackle the system/ Together with Jord Knaap they improved on Barry Wels his ‘
Jaakko Fagerlund is a big fan of Abloy locks and knows a lot about them. And of course he is interested how to tackle the system/ Together with Jord Knaap they improved on Barry Wels his ‘
 The Fichet F3D lock is one of the most intriguing locks that came out in a long time. Not easy to get, quite expensive and contains
The Fichet F3D lock is one of the most intriguing locks that came out in a long time. Not easy to get, quite expensive and contains 
