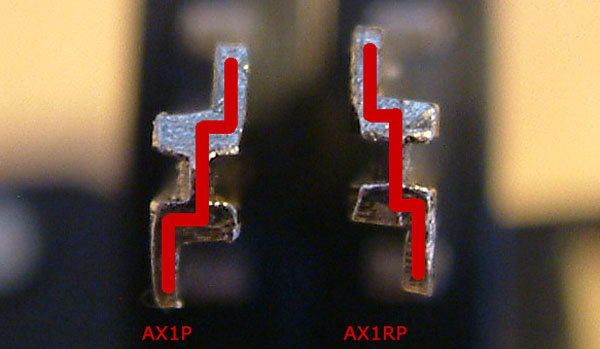
An image can say more then a thousand words ….
I guess by now quite some people are comparing their key to the above image, hoping their key has the same profile as the AX1RP blank (on the right)…..
Why?!?
In cooperation with Kassa TV and one other organisation we performed a little test. In and around Amsterdam we tried to open over 150 bicycles. We got help from random bicyclists, bike shops, and even received assistance from local law-enforcement. Result: we managed to open around 50% of them….
By far the most interesting and intriguing thing we found is that almost all locks we could open used the so called ‘standard key profile’ (blank AX1P). Locks using the ‘mirror image profile’ (AX1RP) seemed almost impossible to open. And we are still investigating why. And we do warn people the flaw might be exploitable in the mirror image profile someday soon … many people are now looking into it, and it could be a matter of time. But for now it seems ok …
One other interesting fact: we managed to open almost all 583 models (over 90%), as well as a high percentage of SL7 and SL9 locks…. if they used a ‘standard key profile’ that is. And a lot of SL9 locks were equipped with a mirror image profile.
Axa by now admits more locks are vulnerable as they expected before, and they will come out with a report themselves any day now. Curious if they found the same things we did (in our relatively small test).
More about this test and the findings (in Dutch) on Kassa TV or http://toool.nl

In my own little test I encountered a lot of those AX1RP locks. More than 50%.
Hi Eelco,
I guess a lot of SL9’s then? Or maybe solid’s? Relatively new bikes?
So what exactly is the design flaw? driver pins too thick?
Cheers,
mh
MH: nice one …
These locks use wafers so there is no driver pin …
Ah, so it’s overlifting of sloppy-tolerance wafer locks. I can imagine why it works better on one type of the keyway you show in the picture, at least if you can turn it only one way. If you had to turn the key the other way, the other keyway would probably more insecure.
Are you doing only blackbox testing on these, or when can we expect so see the first cutaway models that show the effect?
🙂 mh
There is a similiar exploit on youtube for search terms, look for Chip Shuhart ‘dimple lock picked’. he simply fills the keyhole with a tool that takes up all the space except for a place for the tensor, then he swiftly pulls the tool out, releases tension somewhat and reapplies tension.
So Im wondering how many dimple type locks are vulnerable to this type of exploit with keyblanks and tensors with perhaps a bit of the blank shaved off to allow for the tensor to fit in.